Block storage device
The Internet is more and more developed, and the speed of the Internet is getting faster and faster (more and more strict control). Many things can be solved through networking. Many storage industry businesses also get this point. The following figure is a minimalist model, a merchant storage device (black box), a user laptop, and an iSCSI protocol over TCP/IP. For Linux users, you can see a block device /dev/sdax just like using a local hard disk. (like /dev/sda), you can partition it, format it as a file system, or read or write directly to a bare device.
Figure 9 block storage device
For users, this is enough, it is really convenient, pay for it.
For a purveyor of coders, we need to see what is inside this black box. The following figure is the contents of the black box, once again stressed that including the illustrations and descriptions before or after this article are very macro. Limited space can not be said too thin, in line with the main purpose of this article; In addition, to say too much will be similar to the specific business products, I can not do that.
Put aside hardware, drivers, OS, etc., look directly at the software logic. Firstly, the hard disks on the system are composed of multiple RAIDs, how to group, what kind of RAID, what kind of disks constitute RAID, etc. These can be configured by the administrator. . Someone asked (yes, or the person who asked the question earlier): "Not a RAID row?"
Yes, but there is a risk that if a disk fails, RAID will not be able to provide services for the time being, and all users of the entire system will be affected. If multiple RAIDs are formed, only RAID with faulty disks cannot be serviced at the moment, and other RAIDs can continue to work without affecting all users. In the words of a crosstalk performer, the user is a food and clothing parent.
Continuing to look at the figure, the software manages RAID, and provides services to users. It provides users with LUNs (full name is Logical Unit Number, or logical unit number). Of course, users (people) do not have to understand What is a LUN, as mentioned above, is at best a /dev/sdax, LUN is the software, protocol level things. How to understand? Each LUN is associated with a set of physical storage resources. You own this LUN and you own the physical storage resources. If you use physical storage resources, you need to provide your LUN ID. People with programming experience are easy to understand and very similar to a file or socket handle. The client (here not using the word user, here only partial program) to read and write LUNs, at least need to provide "LUN ID + R / W + Offset + Length [+ data]" this information.
Why do I need LUNs instead of "dropping" RAID directly to users?
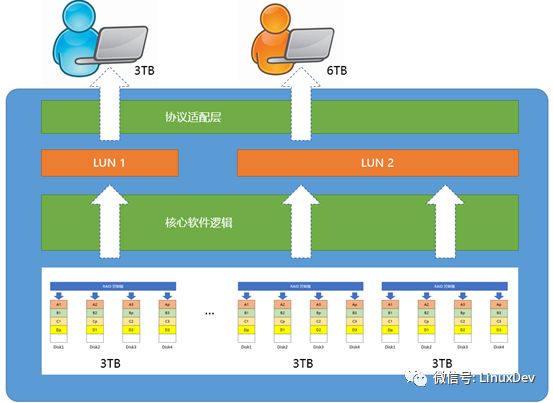
Figure 10 Block Storage Device Internals
Because each user's needs are different.
The code farmer Li Ergou, all worth of 800G code, do Google development and then copy and paste. A geek, with massive HD movies, 4TB+ not to mention. According to Figure 10, we can assign LUN 1 to Li Ergou and LUN 2 to an otaku. The software logic layer is responsible for mapping. In fact, one LUN can be mapped to multiple RAIDs. Multiple LUNs can also be mapped to one RAID (not commonly used because RAID failure affects multiple users). User data is accurately saved to The physical storage resources of this LUN do not appear to be in the state of wearing a crown. When user needs change, such as Li Ergou also began to collect high-definition movies, the space needed is large, then you can expand LUN1 resources, very flexible. Finally, the size of the LUN is the same as the size of the physical storage resource mapped by the LUN and the size of the user's view of /dev/sdax.
Storage device with file system
In fact, in most scenarios, users are formatting devices into a file system. Then the equipment manufacturer said to the user: "I have a way, you can not have to format, I directly provide a file system, mount directly on the line, NFS, simple."
"Yeah!"
"However, we must increase money."
"..."
We don't care about business first. Look at the picture below. Users pay good money and are told that an address is directly mounted to the local site. It is indeed convenient.
Figure 11 Storage device with file system
This time, what is in the black box?

Figure 12 Storage device with file system
After watching the map, is it the same feeling as me? MMP profiteers. One more file system layer, internal formatting LUNs, and then overcharged a lot of money.
If you think only this is wrong!
We assume that you paid for 1TB of space and that the service provider did not really reserve 1TB of physical storage for you. When you use it, apply for physical storage resources. You are angry and you have 1TB full. At this time, you think that you really consume 1TB of physical storage resources from service providers? not necessarily! It is possible to consume only 0.8TB or less.
Aside from commercial stereotyping, from a technical point of view, there are two technologies that need to mention compression and deduplication, which are easy to do at the file system level.
Compress
As you probably know, the file system is performed in blocks of a certain size during IO, taking 4 KB as an example. Compression also uses this data block as a unit and compresses the data before it is written to the disk. The original 4 KB of data may become 2 KB after compression, and the compressed data blocks are again converted into 4 KB and then saved to the physical disk. This operation saves physical resources. When the user reads the data, if it is compressed, it needs to be decompressed first and then returned to the user. The compression and decompression operations are purely algorithmic and mainly consume CPU resources. Therefore, it is not recommended to enable the compression mechanism when the system load is high. In addition, whether the data is compressed requires additional metadata records, which increases system complexity. Some devices will be compressed, decompression operations to the hardware to complete, reducing the CPU consumption.
Deduplicate
Upload a large HD movie to the web disk, seconds pass, encountered it? This shows that the service provider storage system has a file exactly the same as yours. You have met a like-minded housemate. To save space, the system just gives you a tag (or a soft link like that) and then increases the reference count of the file so that others will not affect you. This is still a deconstruction from the document level and it is also very easy to understand. We make an extreme assumption that if two 1G files are only one byte different, they can't be re-educated according to the above method, or they must be uploaded. As part of the document can not be de-emphasized?
The answer is yes. Deblocking at the data block level.

Figure 13 Data block level deduplication
We look at Figure 13 to speak. Initially, there was no hard disk drive, and all of the data in file 1 was written to the hard drive. This is nothing to say. Then, file 2, where BEF three blocks, the hard disk already exists, does not have to be written, and the remaining blocks need to be written. Finally, see file 3, the first 3 blocks, XYZ does not exist in the hard disk, you need to write. The XY behind does not have to be written, and the last E does not have to be written.
Deduplication technology does save physical storage resources, but there are also some problems.
For example: how to determine the current block to write hard disk already exists?
It is not possible to compare hard drives one by one!
One approach is to perform HASH calculations on blocks that were written earlier, and save HASH values ​​and block information into memory. As a Cache, the newly pre-written block calculates the HASH value. If the HASH value exists in the cache, then the block information in the cache is taken out. , do re-operation, record information. Limited memory, Cache can not be large enough to save all the hard disk block information, so the weight is limited, in addition to the Cache update is also a technical point, which Cache update algorithm can be a good deduplication efficiency is a worthy in-depth study topic of.
Well, the above briefly introduces two storage devices. Next...
Someone asked (Yes, still the person who asked the question earlier):
“I asked the father of Wang Ernong Li Ergou his father, Wang, and asked him a question. It is a bug in the software. If this software crashes, isn't all users able to access it?â€
"Yes!"
"Weakly burst, right?"
In the description of the previous RAID, you can realize the word "redundancy". Redundancy plays a role in insurance and protection. Since there are bugs in the software and it may hang, put two copies in there. Two physically independent devices run the same software, and each is the main backup. When the active device is working, the standby device is on standby. The configuration and status of the RAID, LUN, etc. in the active/standby shared system are suspended. The active device is suspended and is on the standby device. The user is unaware. This type of solution is also common in many areas (such as communications equipment).
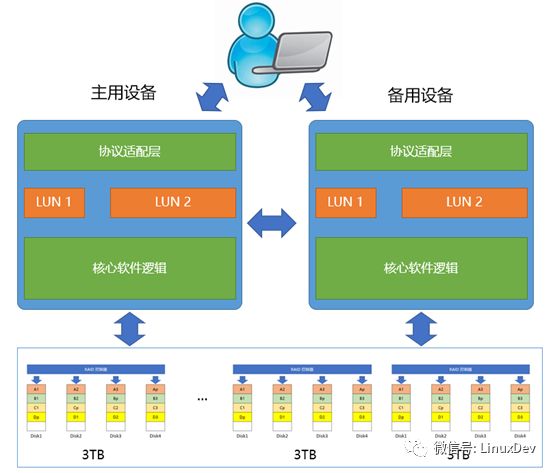
Figure 14 master and backup
"It seems to be useful. Where are your main and standby devices?"
"Service provider's room or data center."
"If the data center caught fire or something else, these devices couldn't provide service?"
"Yes!"
"Weakly burst, right?"
The data center is a place with nets, electricity, and air conditioners. It has a good place for exporting geeks. It is a place with basic fire prevention, anti-theft (anti-brothers?) and other disaster prevention places, but everything will not be pre-prepared. A mistake can be a big deal.
In fact, data centers also have "backups." Generally, in other parts of the city, there will also be a data center for backing up the data in the current data center, drawing fiber closer to the city, leveraging backup efficiency, and even real-time backup.

Figure 15 Data Center
"If the city suffered a major earthquake and both data centers were damaged, will the data be lost?"
"Yes!"
"Weakly burst, right?"
Two centers in three places. That is, the production data center, the city disaster recovery center, and the remote disaster recovery center construction plan. The three data centers in the two cities are interconnected. If a data center fails or fails, other data centers can operate normally and take over the core business or all services.

Figure 16 Three centers in two places
"Then if both cities are..."
"You wait, I'll call."
Hey, what is the company? This is my personal asset certificate. I helped me personally and told me that I was bankrupt.
......
All the world is spread banquet. This is the end of this sharing, or the phrase, the limited level of general energy, ignoring some of these things, if there is such a sentence to evoke your interest, I am very pleased.
Note: We respect the spirit of inquisitive knowledge, and the above remarks made by Daisei Company are purely nonsense.
end
"You can scare me. Looking at the article on the Linuxer public number, learning from the big cows, I always feel that the technology is not growing and my heart is very weak."
“Looking at your physique shouldn’t be just a guilty conscience? Indeed, these articles are of high quality and worth learning. Apart from the “Large Storage,†it’s a bit soy sauce. Isn’t there any need to sneak in to learn?â€
"Get used to it. There is no way to look at the things that interest you."
"I can only talk about it. The one I'm watching is going online. I'll go first. This mobile hard drive is for you to use."
"What's inside?"
"Of course it's something you're interested in - you know."
Do you know the difference of Yoga Laptop and 2 in 1 laptop? No. 1 is yoga notebook with 360 flip rotating absolutely; No.2 is laptop yoga slim is just like normal Education Laptop-connecting screen with keyboard, but 2 in 1 laptop tablet with pen is separately, you can use the monitor part as a window tablet. In one word, every intel yoga laptop have all the features and function of tablet 2 in 1 laptop except separated screen and keyboard. From the cost, windows yoga laptop is much higher than 2 in 1 type., cause usually former with more complicated craft and quality.
What other products you mainly produce? It`s education laptop, Gaming Laptop , engineering laptop, Android Tablet, Mini PC and All In One PC. You can see more than 5 different designs on each series, believe always have right one meet your special application or your clients demands. Therefore, what you need to do is just to get all the requirement details from your clients, then share the complete information with us, then we can provide the most suitable situation.
Of course, you can also call or email or send inquiry of what you need, thus can get value information much quickly.
2 In 1 Laptop,2 In 1 Laptop Sale,2 In 1 Laptop Tablet With Pen,Tablet 2 In 1 Laptop,2 In 1 Laptop Deals
Henan Shuyi Electronics Co., Ltd. , https://www.shuyielectronictech.com